Continuously Manage
Your Threat Exposure.
See every asset, spot every risk, and act before attackers do.
Deepinfo gives you continuous visibility, actionable intelligence,
and clarity to act with confidence.
REQUEST DEMODeepinfo gives you continuous visibility, actionable intelligence,
and clarity to act with confidence.
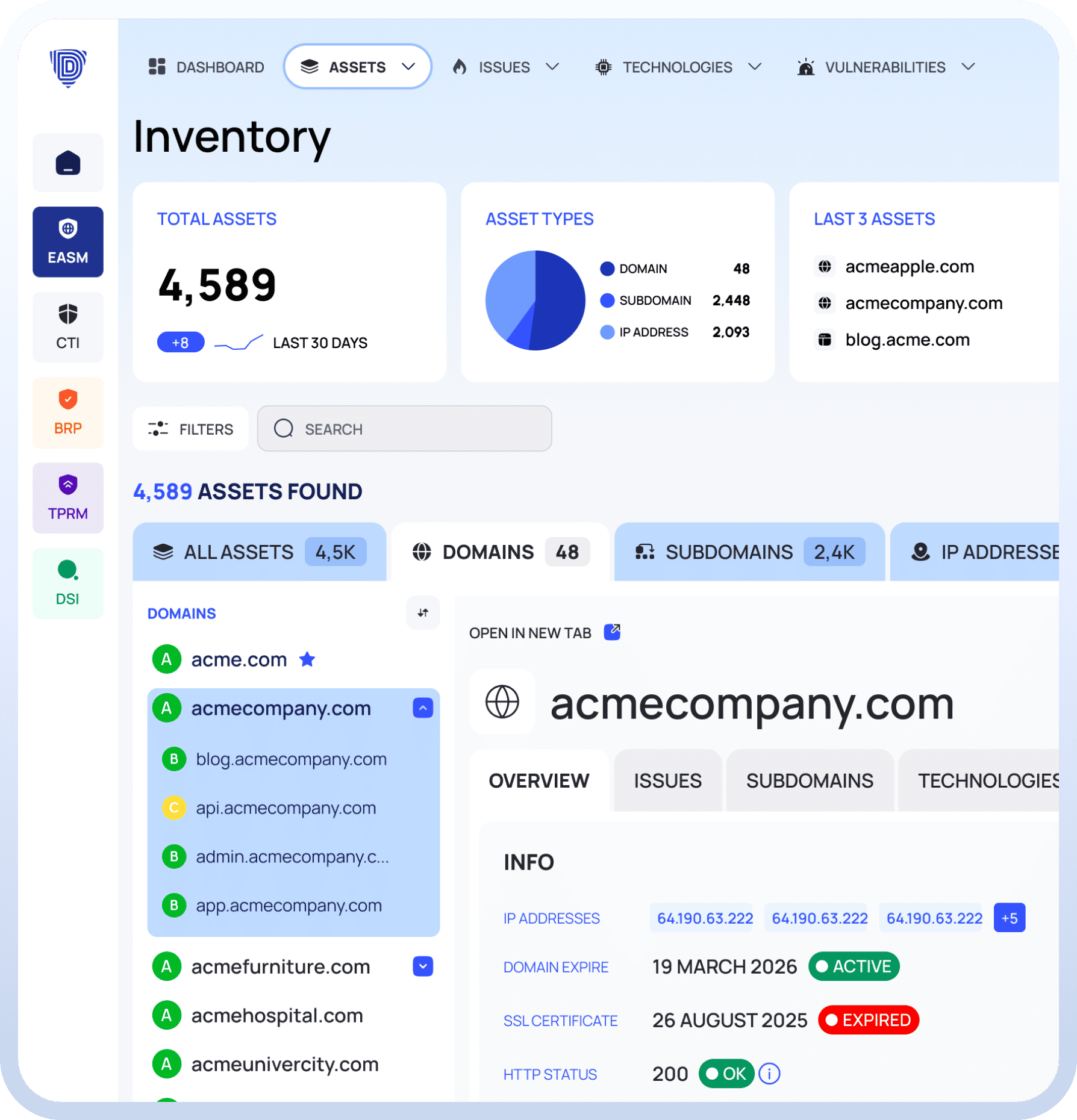
External Attack Surface Management
Discover, Monitor, Secure Your Attack Surface.
Discover every Internet-facing assets.
Continuously scan domains and IPs.
Detect and prioritize critical risks.
Remediate issues with clear guidance.
Understand risks with transparent scores.

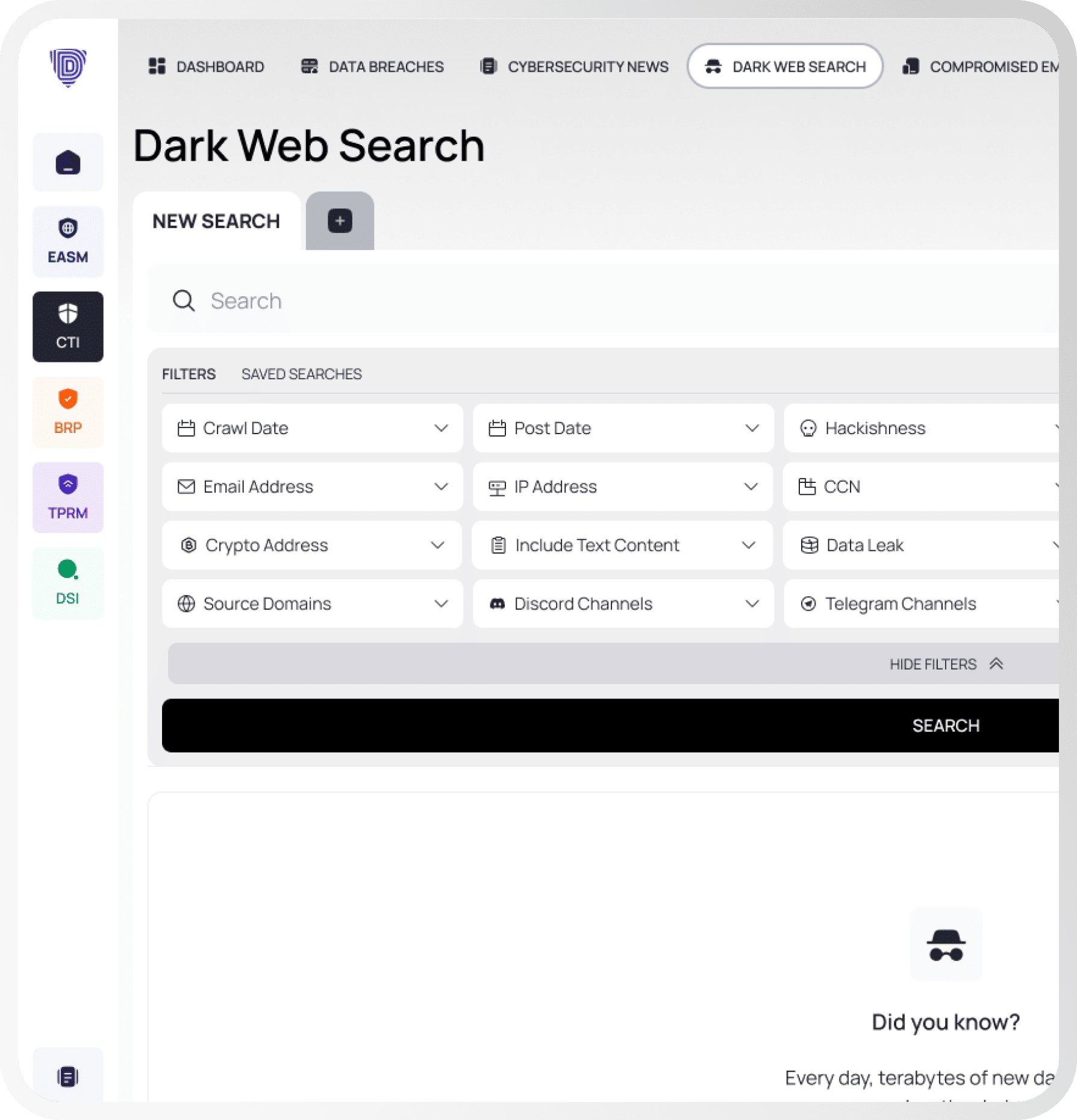
Cyber Threat Intelligence
Uncover Threats, Enhance Security.
Search the dark web for threats.
Track mentions across the dark web.
Detect employee email breaches.
Identify compromised employee devices.
Find client credentials in breaches.
Detect exposed payment information.
Track threats targeting executives.
Analyze threat actor tactics.
Explore the historical breach index.

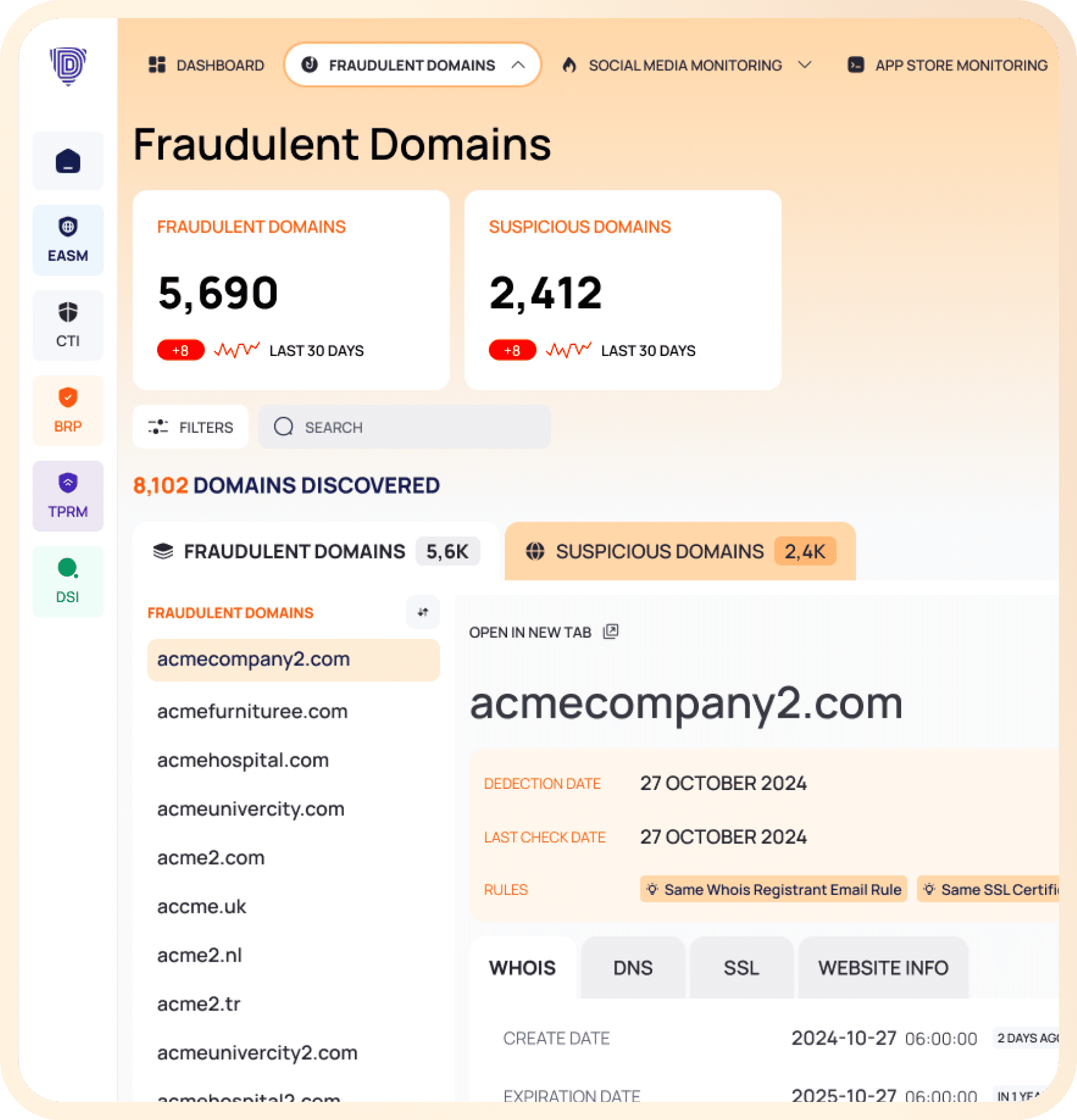
Brand Risk Protection
Keep an Eye on the Internet, Protect Your Brand.
Detect fraudulent and look-alike domains.
Monitor social media for threats.
Detect fake apps using your brand.
Watch search engines for abuse.
Remove brand risks with managed takedowns.

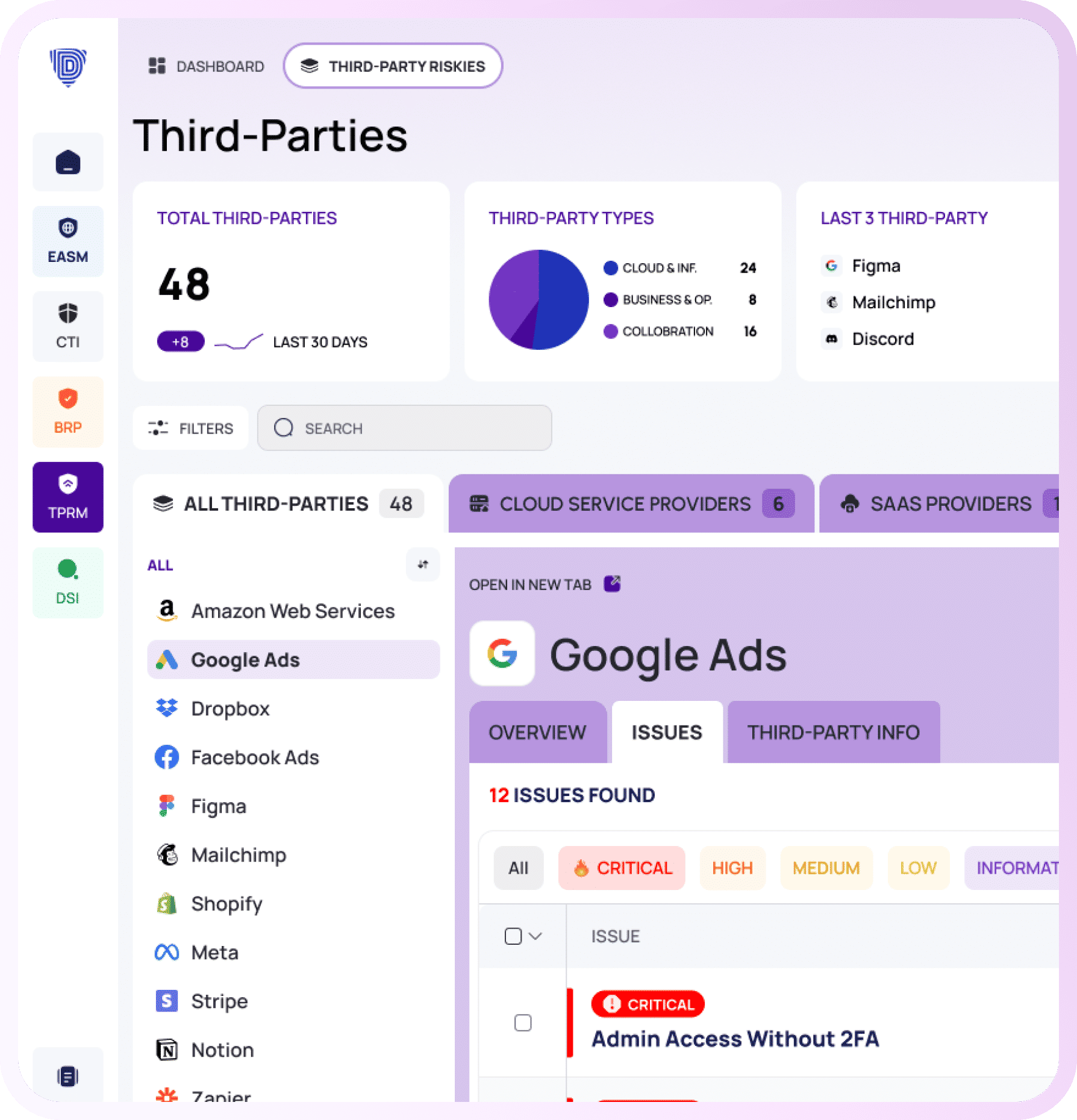
Third-Party Risk Management
Secure Your Supply Chain, Strengthen Your Security.
Identify third-party relationships.
Continuously monitor vendor posture.
Run comprehensive risk assessments.
Track compliance across frameworks.
Generate automated vendor risk scores.

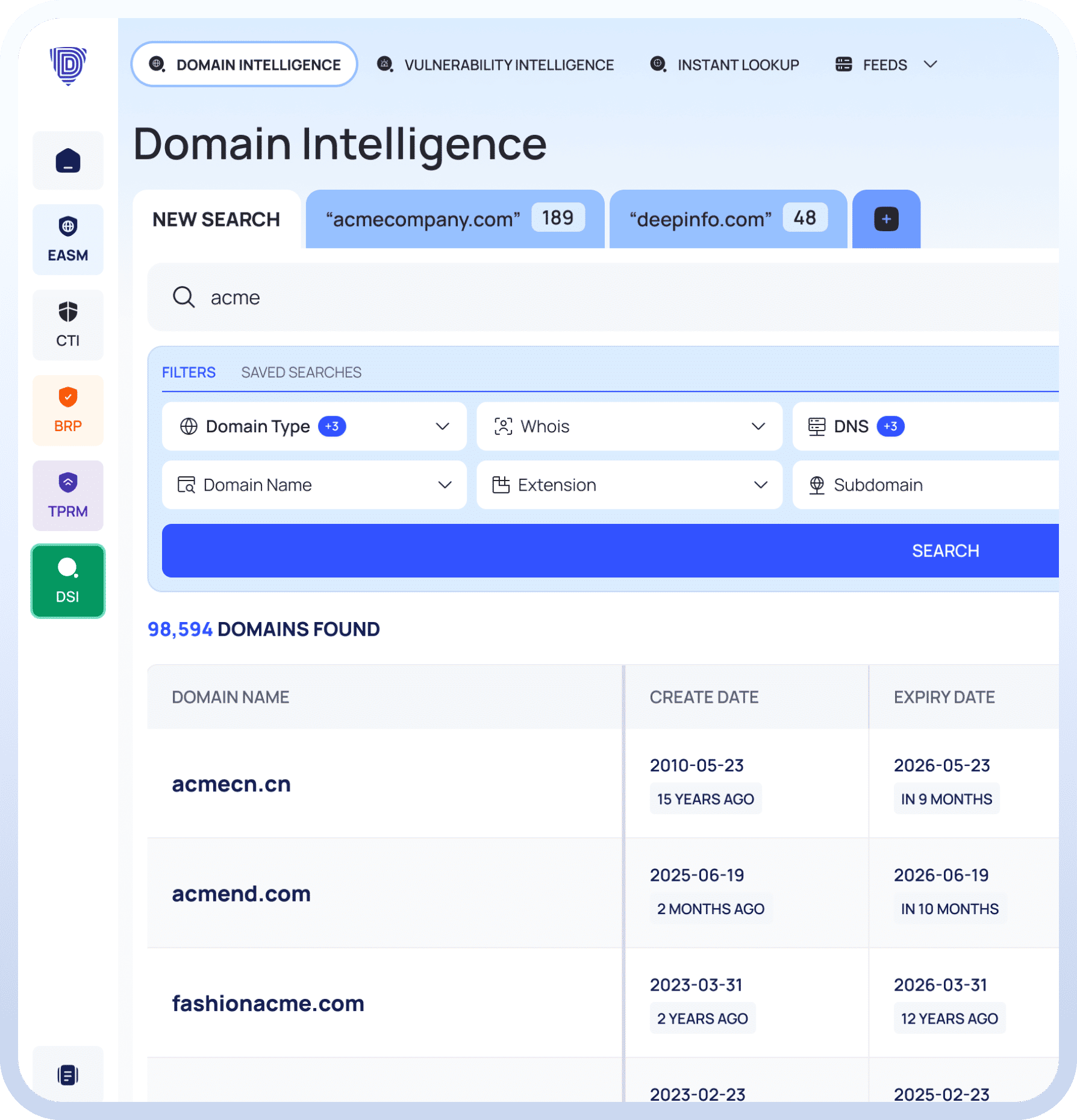
Deep Search & Insights
Dive Deep, Reveal Actionable Intelligence.
Search every domain with historical data.
Explore vulnerabilities with detailed intelligence.
Use IOC feeds for detection and protection.

PLATFORM
Continuous Threat Exposure
Management Platform
Continuously detect, analyze, and mitigate threats across your digital landscape.
DATA & API SERVICES
The Most Comprehensive Internet Data at Your Service
Request Demo
Trusted by leading companies worldwide, the Deepinfo Security Platform is the preferred choice for continuously managing cyber threat exposure.





